Let us burst a myth and explore how we can set up an Envoy Proxy API Gateway with Gloo Edge in a hybrid cloud infrastructure with Amazon EKS Anywhere (EKS-A) and connect an AWS Lambda function using Gloo Edge.
The myth is that API Gateways are for cloud or can only with be used with public cloud providers, but that is not the truth. API Gateways are suitable for any architecture public, private, or hybrid cloud. The only basic requirement is to have an API.
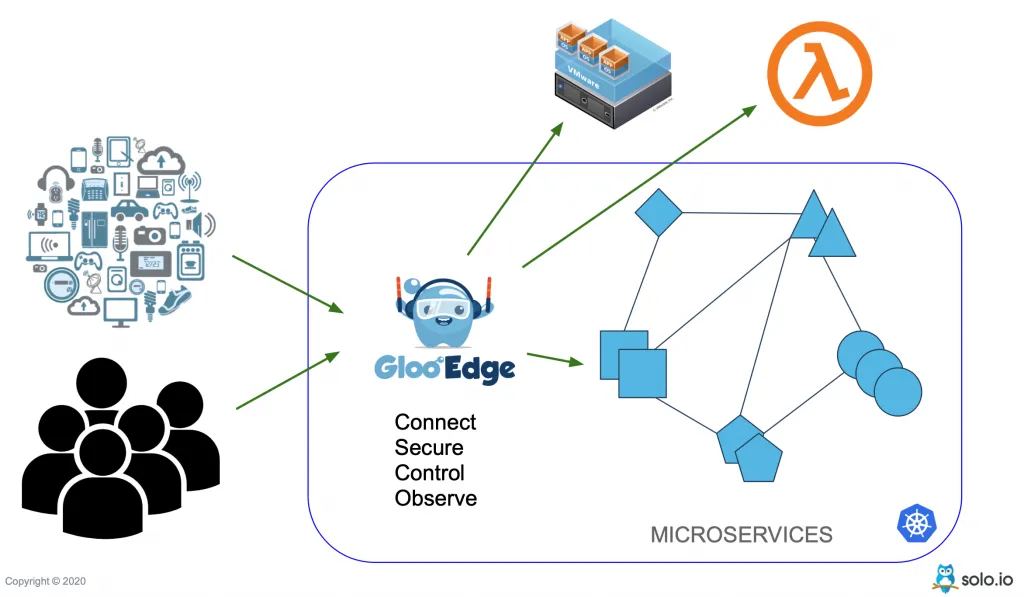
Gloo Edge is an open-source, flexible, and extensible API gateway built on Envoy Proxy for microservices Kubernetes (K8s) environments. Gloo Edge configures the behavior of the Envoy Proxy data plane to ensure secure application connectivity and policy based traffic management.
What do we need to set up EKS-A and Envoy Proxy?
Cloud Infrastructure
- VMware Cloud (VMC) – infrastructure to deploy an
eks-aKubernetes cluster - an AWS account – with permissions to create and execute AWS Lambda functions
Tools
You might also need a Gloo Edge Enterprise License Key to deploy Gloo Edge on to the EKS-A infrastructure.
Demo Sources
To start, clone the demo sources from the GitHub repository:
For convenience, we will refer the clone demo sources folder as $DEMO_HOME:
Create an environment to run EKS-A and Envoy Proxy
We will set the following environment variables for convenience, and we will be referring to these variables in the upcoming sections:
Build an EKS-A cluster for use with Envoy Proxy
To create the EKS-A cluster, run the following command:
gloo-edge.yaml– will be generated using theeks-a generatecommand. For more information on the command please refer to the docs.
Configure Storage Class
The demo clusters does not have any default storage provisioners or storage class defined. For this demo we will use Rancher’s local-path-provisioner:
Wait for the storage provisioner to be ready:
Once the provisioner is installed, check the same using the command kubectl get sc:
As you have noticed from the command output, local-path is not the default storage class. A default storage class helps in dynamic provisioning of the Kubernetes Persistent Volumes.
Let us set it as the default storage class so that any new PVC requests will be created using this Storage class’s underlying storage:
Running the kubectl get sc again shows the local-path as the default provisioner:
Install Gloo Edge Enterprise
Download and install latest glooctl by running:
Add glooctl to the system path:
The Gloo Edge proxy is a Kubernetes service of type LoadBalancer, for the purpose of this blog we will configure it to be of type NodePort using the install-ee-values.yaml as shown below:
- Use
30080as NodePort to access the Gloo Proxy - Use
30443as NodePort to access the Gloo Proxy
NOTE:
You can safely ignore the helm warnings; it will take few minutes for Gloo Edge to be ready, try the command glooctl check to verify the status.
Once Gloo Edge is deployed check if Gloo Edge is functional:
A successful Gloo Edge installation should show an output like:
Deploy an AWS Lambda Function
Now that we have created an EKS-A cluster and deployed Gloo Edge on it successfully, let’s create an AWS Lambda function and use Gloo Edge to invoke it.
Create AWS IAM Role
Save the Role ARN environment variable:
Attach the AWSLambdaBasicExecutionRole to our role:
Create Lambda Function
The demo is ready to deploy a simple node.js “hello world” application:
Let’s deploy that function using AWS Lambda:
Let’s make sure our function works:
If the function has executed successfully, the $DEMO_HOME/response.json should have the following content:
Using Gloo Edge for EKS-A and Envoy Proxy
Since we have now deployed the AWS Lambda function, let’s now create the necessary Gloo Edge resources that will allow us to configure and access the Lambda via Gloo Edge Gateway. To have more understanding on some of the core concepts, check the Gloo Edge documentation.
As part of this short demo we will:
- Create an AWS Secret
- Create a Gloo Upstream
- Create Gloo Virtual Services
Create an AWS Secret
We need to create a Kubernetes secret that holds the AWS Keys. This secret will be used by Gloo Edge invoke the AWS Lambda function:
NOTE: If you have not set the environment variables $AWS_ACCESS_KEY_ID and $AWS_SECRET_ACCESS_KEY, the value from $HOME/.aws/credentials will be used.
You can check the created credentials by running:
Create an upstream resource
As part of this section we will create a Gloo Upstream that will allow the Virtual Service to talk to AWS Lambda via Gloo Edge Gateway,
IMPORTANT: If your default region is other than us-east-1, ensure you set the value for $AWS_DEFAULT_REGION to the region of your choice before running the upstream create command.
Check the status of the upstream resource:
Create a route
A route is a Gloo Virutal Service resource that allows us to access the API, i.e. the services that are deployed on to Kubernetes.
- Domains that will be allowed by the gateway
- The prefix to access the API
- The destination spec type
- In this case, an AWS Lambda function named
gloo-edge-hello-lambda - The upstream that wil be used to route the request
Let us create the virutal service:
Check the status of the virtual service:
Gloo Proxy URL
We need to use the Gloo proxy to access the API, we can use glooctl to get the proxy URL:
IMPORTANT:
glooctl proxy url always returns the hostname of the Kubernetes nodes. You can check the hostnames using the command kubectl get nodes
Resolve Nodes via /etc/hosts
NOTE: You can ignore this section if your nodes are resolvable by their names.
We are assuming that your VMC environment does not have a DNS resolver to resolve the EKS-A Kubernetes node names. In such cases we need to add the node names to the /etc/hosts file for them to be resolved.
Invoke Function
Check if the API is accessible:
NOTE:
We have to use the host header ‘Host: example.com’ as we have restricted the gateway domains of the Virtual Service to example.com only. In the next chapter we will use the wildcard domain that will allow all the domains.
The command should return a list of fruits as shown,
TIP:
Try the same request as show below to see the other response headers http POST $GLOO_PROXY_URL/greet 'Host: example.com' user=tom
Cleanup
Detach policy,
Delete the Role,
Remove entries from /etc/hosts file,
Summary
As part of this short blog we explored how to:
- Create an EKS-A cluster
- Deploy Gloo Edge
- Use Gloo Edge to invoke an AWS Lambda function
Gloo Edge is not restricted to AWS Lambda, it can also be used to connect traditional applications and Kubernetes microservices. Head over to our workshops to learn more things you can do with Gloo Edge.
Read our other blogs about how Solo works with Amazon EKS Anywhere:



























%20a%20Bad%20Idea.png)











%20For%20More%20Dependable%20Humans.png)











